- Reconnaissance Attacks
- Access attack
- Denial of Service Attack
- Worms, Viruses and Trojan Horses
The purpose of an attack would be to compromise and cripple a system such that it would take a long time to be able to fully repair to system.
A reconnaissance attack would be mainly about learning information relating to a target network by using publicly available resources, eg: Company's website, employee's profile, etc. Gaining the IP address of the company as well as the domain name would also be part of such an attack.
Although such an attack seems fairly harmless, it allows the perpetrator to gain information about the network such as which IP addresses are in use, the times of inactivity and which ports are active. Furthermore, the intruder would also be able to determine to type of application and operating system used by querying the ports. With this information, the attacker would then be able to plot an attack at the times of lowest security i.e. times of inactivity and hence perform a DoS attack such as a ping of death.
Reconnaissance attacks cannot be prevented entirely, but there will be signs of recon attacks that intrusion detection systems (IDS) can determine such as ping sweeps and port scans, and hence the administrator would be able to minimize the damage done to the system in the actual event of a DoS attack preceding the recon.
This is an example of port scanning.
This is an example of an intruder gaining IP address and domain name information about an organization.
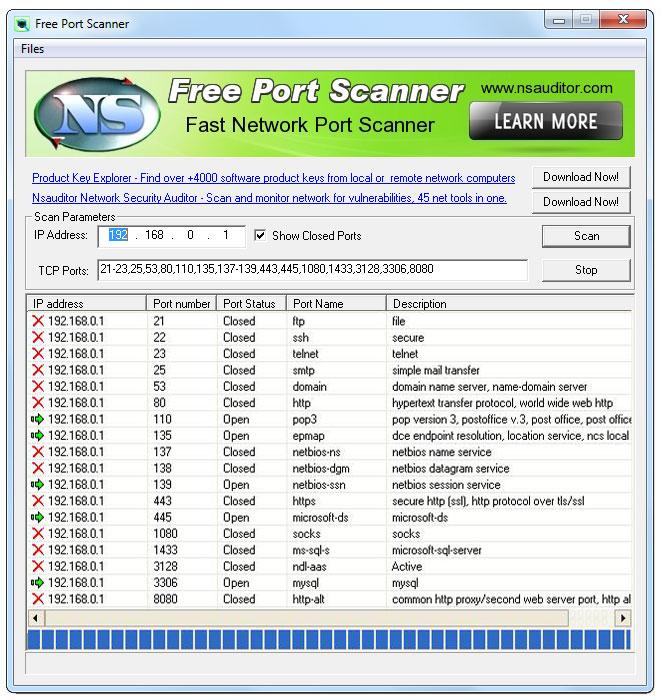

Hi bingjie, thanks for the post on common networking attack threats and solutions. I now know more about the threats in a network. I also learned about the different attacks you can execute on a computer such as port scanning to see which port is open to attack and etc, although i will not be a hacker myself. The usage of diagrams also helped me to understand and roughly grasp the interface of port scanning and etc.
ReplyDelete