However, in the implementation of IPSec, there are many complex features to make consideration for. One reason for such complexity is that the IPSec provides mechanism, not policy. Instead of a an encryption algorithm or authentication function, IPSec bases itself on a framework that is able to provide almost any service that both ends require.
Although there are many more protocols, this post will only depict 3 of them.
One protocol used by IPSec is the ESP, or Encapsulating Security Payload. This protocol encapsulates, or surrounds the data, encrypting it, ensuring that the data payload sent over is in an unreadable format. Overall, this protocol is able to provide data confidentiality, integrity, limited traffic flow confidentiality and anti-replay protection. Although this protocol does not protect (encrypt) the IP header, ESP ahas an authentication function, but only for its header and encrypted payload.
The AH, Authentication Header sends its payload in clear text, as this protocol does not provide file encryption service. Instead, the AH's main purpose is to authenticate the payload, and technically, it is possible, though rare, to use both AH and ESP together, essentially providing authentication and encryption. Hence AH is able to provide data integrity through authentication that uses a keyed-hash mechanism, origin authentication - confirmation that packets definitely originated from peer router. It also provides optional replay protection - replay is a form of attack in which perpetrators capture data physically from cables/ wires and re-inject the data back into the wire at another time.
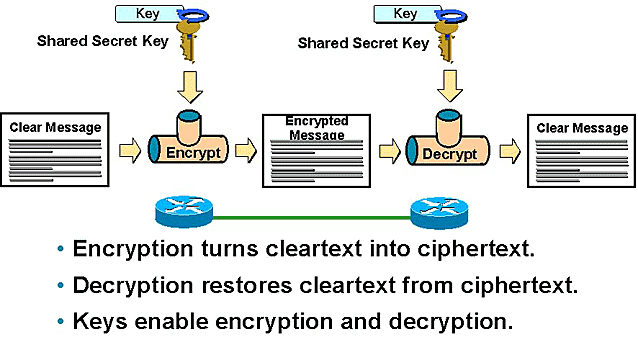
DES, Data Encryption Standard encrypts the payload data as well. It uses matching shared secret keys on each peers and also includes encryption/ decryption algorithms. A DES encryption process is as such
- Firstly, a shared secret key is appended to the algorithm, the payload is then submitted into the algorithms in fixed-length blocks and then converted into cypher-text, i.e. encrypt.
- The encrypted data is transmitted to the IPSec peer via the ESP.
- The peer receives the ESP packet, extracts the cypher-text, decrypts it through the decrypting algorithm which reveals the payload in a readable format.
The following picture shows the DES in action.
References:
No comments:
Post a Comment